Anti-phishing Guidance: Difference between revisions
| (3 intermediate revisions by one other user not shown) | |||
| Line 3: | Line 3: | ||
== '''To protect our customers from phishing attacks, we recommend the following general measures''': == | == '''To protect our customers from phishing attacks, we recommend the following general measures''': == | ||
[[File:Phish.png|right|frame|caption|link=|Example phish link]] | |||
* '''Hover over any | * '''Hover over any website address before you click.''' This will allow you to see the actual address of the website, even if it is disguised by a fake address. | ||
* '''Copy and Paste''' Sometimes the hover does not present anything. You can also right click and copy the address. Paste it into a notepad or text editor to examine whether it is legitimate or not. | * '''Copy and Paste.''' Sometimes the hover does not present anything. You can also right click and copy the address. Paste it into a notepad or text editor to examine whether it is legitimate or not. | ||
* '''Be cautious with unknown senders.''' If you receive an email from someone you don't know, be cautious about clicking on any links or opening any attachments. We recommend you not reply to unknown senders. | * '''Be cautious with unknown senders.''' If you receive an email from someone you don't know, be cautious about clicking on any links or opening any attachments. We recommend you not reply to unknown senders. | ||
* '''Do not install unauthorized software and do not share credentials with anyone.''' Only install software from trusted sources, and never share your login credentials with anyone. | * '''Do not install unauthorized software and do not share credentials with anyone.''' Only install software from trusted sources, and never share your login credentials with anyone. | ||
| Line 27: | Line 27: | ||
In most cases, you can probably ignore it. If it pretends to be from your bank or another vendor you actually have a relationship with, verify by calling them or logging in to your account with the entity but don’t use a link shared via email just to be safe. | In most cases, you can probably ignore it. If it pretends to be from your bank or another vendor you actually have a relationship with, verify by calling them or logging in to your account with the entity but don’t use a link shared via email just to be safe. | ||
== '''Want to know more?''' == | == '''Want to know more?''' == | ||
Latest revision as of 15:36, 9 December 2024
Phishing is a type of online fraud that attempts to trick people into giving up their personal information, such as passwords, credit card numbers, and Social Security numbers. Phishing attacks often come in the form of emails that appear to be from legitimate sources, such as banks or government agencies. Note that XMission and other legitimate entities will never ask for such information via email.
To protect our customers from phishing attacks, we recommend the following general measures:
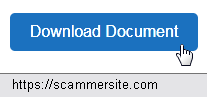
- Hover over any website address before you click. This will allow you to see the actual address of the website, even if it is disguised by a fake address.
- Copy and Paste. Sometimes the hover does not present anything. You can also right click and copy the address. Paste it into a notepad or text editor to examine whether it is legitimate or not.
- Be cautious with unknown senders. If you receive an email from someone you don't know, be cautious about clicking on any links or opening any attachments. We recommend you not reply to unknown senders.
- Do not install unauthorized software and do not share credentials with anyone. Only install software from trusted sources, and never share your login credentials with anyone.
- Use long, complex passwords and a password manager. Your passwords should be at least 12 characters long and include a mix of upper and lower case letters, numbers, and symbols. Use a password manager (e.g. Bitwarden, LastPass, etc.) to help you create and remember strong passwords, and to make your password unique for each login.
- Use social media responsibly. Be careful about what you share on social media, as this information can be used by phishers to target you.
- Deploy multi-factor authentication. Multi-factor authentication adds an extra layer of security to your accounts by requiring you to provide a second form of identification, such as a code sent to your phone, when you log in.
By following these recommendations, you can help protect yourself from phishing attacks and keep your personal information safe.
But what about specific emails that reach your XMission inbox?
Here are some common phishing tricks and examples we see in email sent to our customers:
- Different sender: The “From” email address is different from the official domain (e.g., dom@randomdomainxyz123.com instead of help@officialdomain.com).
- Fake XMission email: The email body looks almost like something we might send but the “From:” and/or “To:” is missing or incorrect, and any links point to a non-XMission website (i.e., clickbait). XMission emails will only link to xmission.com websites and those associated with our billing partner, rev.io.
- Vague or urgent requests: Be wary of vague content or emails that create unnecessary urgency.
- Check for warning flags: Pay attention to alerts from your email client about potential phishing or external senders.
- Report as spam: Anytime you get email you’ve identified as spam or a phishing attempt, please report it to us so we can improve our spam filters and protect others.
What if you’re still uncertain if something is a phish?
In most cases, you can probably ignore it. If it pretends to be from your bank or another vendor you actually have a relationship with, verify by calling them or logging in to your account with the entity but don’t use a link shared via email just to be safe.
Want to know more?
Phishing scams commonly employ a variety of deceptive tactics to trick victims. Here are some prevalent examples:
- Deceptive emails and websites: Phishers often send emails that appear to be from reputable organizations, such as banks, online retailers, or social media platforms. These emails typically contain a sense of urgency, prompting victims to click on a link or download an attachment. However, these links often lead to fake websites that closely resemble the legitimate ones, designed to steal login credentials or other sensitive information.
- Spear phishing: This targeted form of phishing involves emails that are personalized to the recipient, often using their name, job title, or other personal details. This approach makes the email appear more legitimate and increases the likelihood that the victim will fall for the scam.
- Smishing and vishing: Phishing attacks are not limited to email. Smishing uses text messages to deceive victims, while vishing relies on phone calls. In both cases, the attacker attempts to manipulate the victim into revealing personal information or performing a specific action.
- Social engineering: Phishers often use social engineering techniques to manipulate victims into taking the desired action. This may involve creating a sense of fear, urgency, or curiosity. For example, an email might warn of a compromised account or offer a too-good-to-be-true deal.
By being aware of these common phishing tricks, individuals can better protect themselves from falling victim to these scams.
Need further guidance? Contact our technical support department.