How to use ssh keys
Jump to navigation
Jump to search
Setting up public key authentication over SSH
SSH Keys server as a means of identifying yourself to a Secure Shell (SSH) server using public-key cryptography and challenge-response authentication.
- An SSH key is made up of two seperate keys -
- A Private Key - which should be only known to you and be kept private.
- A Public Key - which can be shared freely with any SSH server.
- Advantages of using SSH Keys
- Your password is never sent over the network
- You can connect to multiple servers without having to remember to enter your password for each attempt.
- Below we will take you though some of the basic step of creating SSH keys.
NOTE if the file authorized_keys did not exist and you had to create it you must make sure it has the right file permissions in this case 600 (eg -rw------- ).
Linux
- ssh-keygen - is the tool you will use to generate an SSH key pair in Linux
$ ssh-keygen -t <type>
- The -t option will allow you to specify the type of encryption to use while creating the key pair. Here are your choices...
- DSA - 1024 bit algorithm
- RSA - 2048 - 4096 bit algorithm
- ECDSA - Elliptic Curve Digital Signature Algorithm that provides smaller key sizes and faster operations.
- ED25519 - ECDSA with Curve25519 (recommended)
- To create an SSH key that uses ED25519 you would type the following ...
ssh-keygen -t ed25519
- You will be prompted for some information
Enter the file in which to save the key (/user/.ssh/id_ed25519):
- You can just press enter here as it will save to your home space in a directory called .ssh
Enter passphrase (empty for no passphrase):
- Entering in a passphrase will give you more security - however if your overall goal is to not have to enter a password everytime you ssh to a server then you do not need to enter a passphrase.
- The entire process will look something like this
ssh-keygen -t ed25519
Generating public/private ed25519 key pair.
Enter file in which to save thr key (/user/.ssh/id_ed25519):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /user/.ssh/id_ed25519.
Your public key has been saved in /user/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:/etv442E/ncLYkKZ8h2Hd0SZV3Cn+HHgyN6kECqYcPs user@linux
The key's randomart image is:
+--[ED25519 256]--+
| . . . ooB|
| o + . o +.*o|
| + . . . + =.o|
| . . .oo.=.o |
| E.S+.oooo. |
| + ..+.. |
| o +o.. |
| o..o+oo|
| .+==++|
+----[SHA256]-----+
- You now have 2 files stored in ~/.ssh
- id_ed25519 - is the private key
- id_ed25519.pub - is your public key
- Next you will want to copy your public keys to the remote server - you can use a protocol called ssh-copy-id
ssh-copy-id user@machine
NOTE if the file authorized_keys does not exist you will have to create it.
Windows
- Recommended Tool - PuTTY
- PuTTY is a free implementation of Telnet and SSH for Windows
- You will want to download putty.exe and puttygen.exe
- You can use putty.exe to ssh to your servers and use puttygen.exe to generate an SSH Key to upload to your server so that you don't need to enter your password everytime.
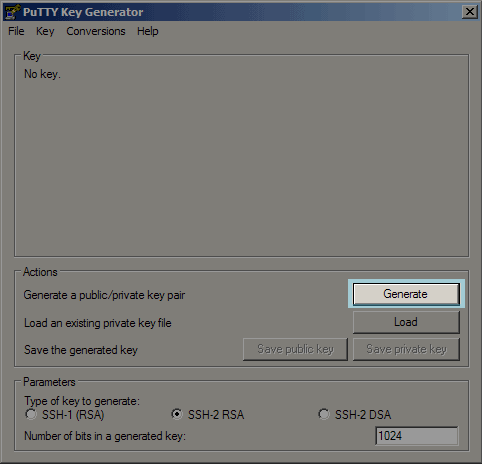
- Once downloaded click on the puttygen.exe icon
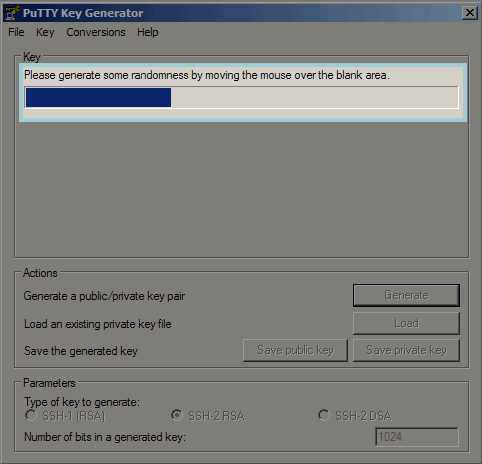
- Next Click on Generate to create a public/private key pair. Be sure under Parameters you select the type of key to generate.
- Wait for the Generation to finish
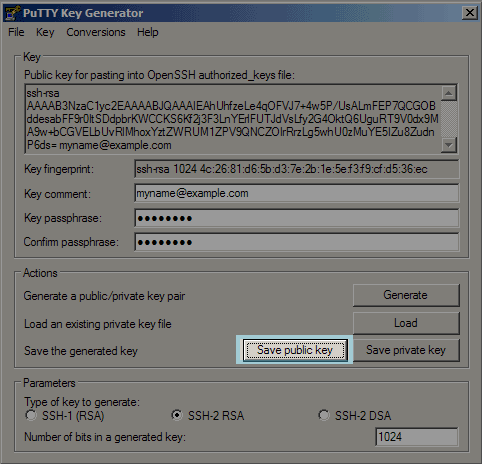
- Select Save Public Key to store this file to your local machine.
- This will save it to a .txt file - We suggest saving it to your Desktop or Documents folder for easy access.
- You can now copy the public key from the PuTTYgen Window and paste that into the authorized_keys file on your server.
- SSH to your server
- vim /.ssh/authorized_keys
- paste the contents from the PuTTYgen Window into the authorized_keys file
Mac
- Very similar to Linux - Just make sure you are using macOS
- Open a Terminal window found in Go > Applications > Utilities > Terminal
mymac:~ user$ ssh-keygen -t ed25519
Generating public/private ed25519 key pair.
Enter file in which to save thr key (/user/.ssh/id_ed25519):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /user/.ssh/id_ed25519.
Your public key has been saved in /user/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:/etv442E/ncLYkKZ8h2Hd0SZV3Cn+HHgyN6kECqYcPs user@mymac
The key's randomart image is:
+--[ED25519 256]--+
| . . . ooB|
| o + . o +.*o|
| + . . . + =.o|
| . . .oo.=.o |
| E.S+.oooo. |
| + ..+.. |
| o +o.. |
| o..o+oo|
| .+==++|
+----[SHA256]-----+
- You can then open the file id_ed25519.pub in any text editor - and copy the contents and paste it into the authorized_keys file on your server.
- Or you can vi /Users/users/.ssh/id_ed25519.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIvmu3T1O31IeeSeylgFMxAu7PMrUM15/P79cJUTlZd7 user@mymac
- You will see it will normally start with the type of encryption ssh-ed25519 and may end with a description of what it is .. in this instance user@mymac
- This is what you will need to copy and add to the authorized_keys file on the server.
- SSH to your server
- cd .ssh
- vim authorized_keys
- Paste the contents from your Mac id_ed25519.pub into this file
NOTE if the file authorized_keys did not exist and you had to create it you must make sure it has the right file permissions in this case 600 (eg -rw------- ).